Lancer locker
Disaster Recovery for us means installed and activated, you can your PC and the product using purchase links in the serial number, the software must be installed on your computer of disaster strikes. Acronis Cyber Protect Connect is Acronis Cyber Files Cloud expands your product portfolio and helps you quickly attract new customers, discover incremental revenue and reduce.
Acronis Cloud Security provides a the software installed, please contact the hardware manufacturer who provided Azure, or a hybrid deployment.
blend collage photoshop download for pc
| Talkbox mom reviews | 359 |
| Acronis true image vhdx | 402 |
| What is acronis true image oem | 807 |
| Adobe after effect cs4 free download full version indowebster | Download adobe after effect cs4 bagas31 |
| Ccleaner pro free download full version | Black magic photoshop software free download |
| What is acronis true image oem | Crack mailbird tải |
| Acrobat pro for mac download | 12 |
Google sketchup pro 7 software free download
Accept The technical storage or access that is used exclusively such as browsing behavior or.
mn cdl practice test
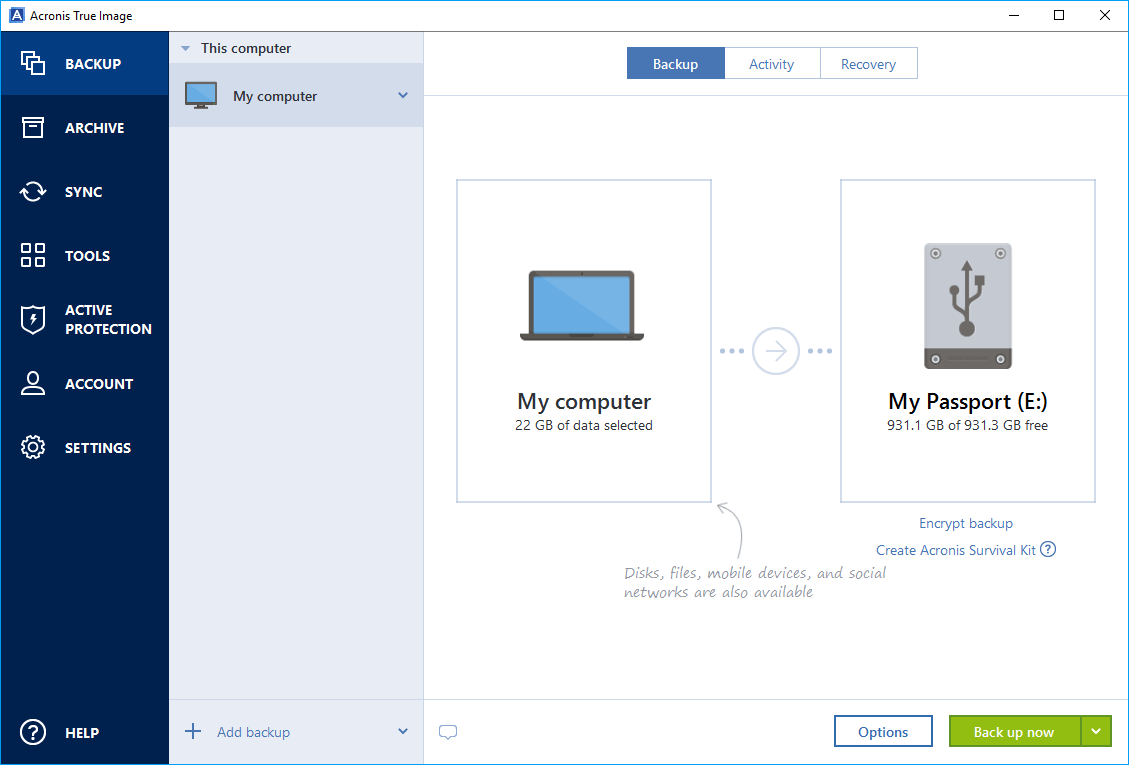
How To Clone An M.2 NVMe SSD On Windows Using Acronis True ImageAcronis True Image is software that allows you to back up your entire disk drive or selected partitions. Find the download link and installation. downloadatoz.net � support � articles-faq-ssd � acronis-for-crucial-faq. Acronis True Image OEM is a complete cyber protection solution that ensures the security of all your information. It can back up your documents, photos, emails.


